Don't fall for these phishing scams: Key Tips.
- Phishing scams use social engineering and urgency to manipulate you into making wrong decisions. 🚨
- You can identify red flags in suspicious emails by checking the sender's address and destination links. 🔍
- Common phishing scams imitate banks or networks social media to provoke fear and get you to act quickly. Verify through reliable methods instead. ✅
Email phishing scams have been around for years, and it's easy to fall for these convincing traps. The best way to protect yourself against social engineering is to stay alert and informed. 🧠
Reasons why phishing scams are effective
One of the most common forms of online threat is the scam. phishing via email. This tactic has been around since the 1990s, and over time it has become more sophisticated. Today's phishing scams are the ones that look very convincing and make you feel like you need to act urgently. These scams use social engineering to trick you into making a bad decision because you think something is at risk. Stay safe from manipulation by educating yourself on what to look for and what to avoid. 📚
Ways to identify a phishing scam
Most people check their email in mobile devices, but if you receive a suspicious email about someone accessing one of your accounts, DO NOT click that “Verify Identity” button in the email, no matter how convincing it looks! ⚠️
Mobile email clients often hide some of the red flags that They use phishing scams to reach your inbox. Whenever you receive a suspicious email, the first thing you should do is check it from a computer desktop, where it is much easier to see the real email address of the suspicious sender. 💻
This example shows what a sender would look like. legitimate email and URL when viewing it in Gmail from a desktop. 📧
Note that the full email address of the sender is displayed at the top of the email. You can also skip the mouse about the sender's email for more information. If there are hyperlinks in the email (such as a "Click here to verify" button), skip the mouse but don't click on the hyperlink to see where it takes you. The URL will be displayed at the bottom of the browser window. browser. 👀
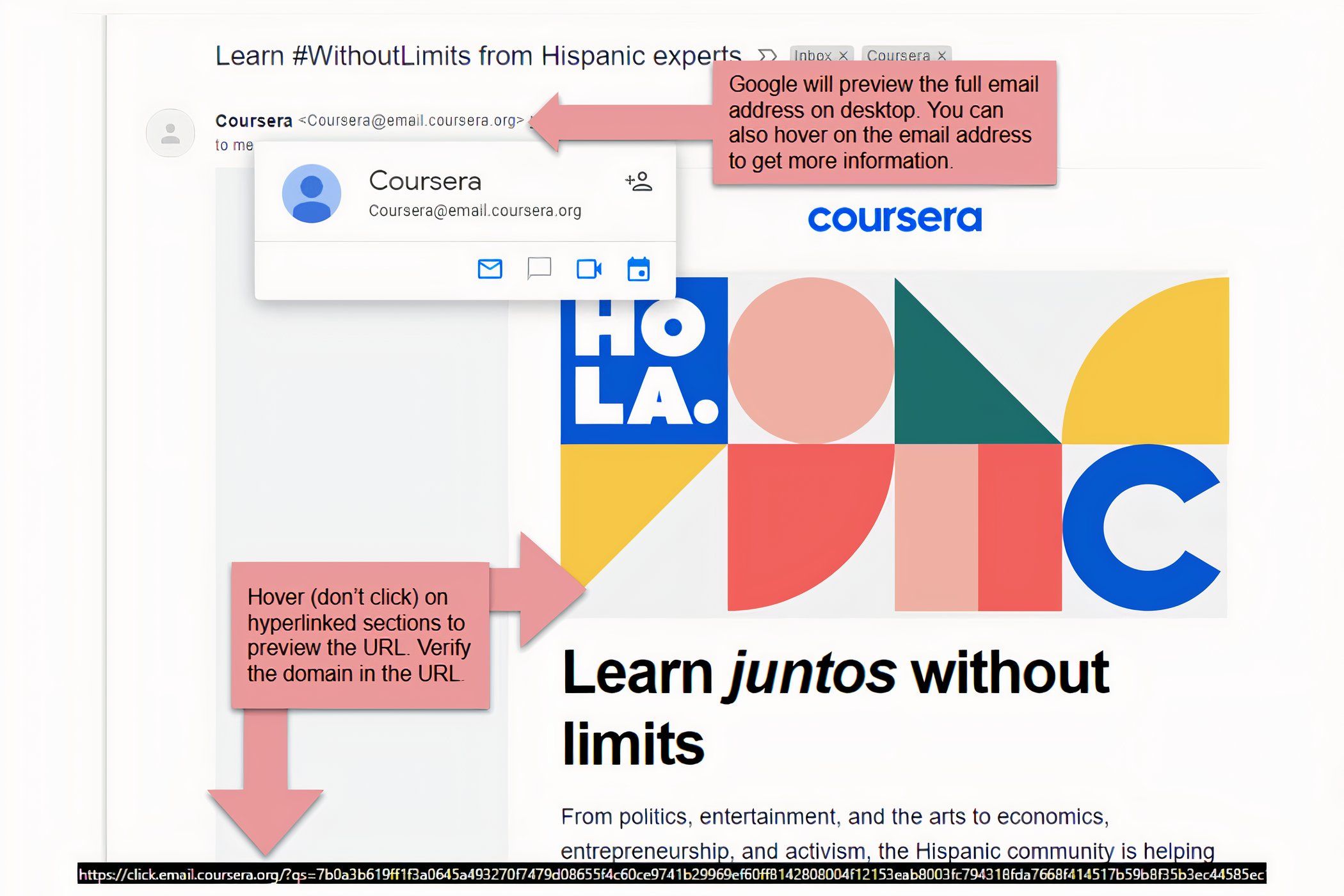
There are obvious warning signs when it comes to identifying a suspicious email. When you see the email in a computer desktop, pay attention to the sender's email address. Does it match the domain of the company it claims to be from? Or is it a long string of strange characters that has nothing to do with the company that supposedly sent the email? ❗
Make sure you always hover over a link in a suspicious email to preview the destination. If the link takes you to a long, suspicious URL that doesn't contain the company's actual domain, it's most likely a scam. In general, you should never Clicking on links in an unexpected email. Instead of using the link provided, open a new browser window and log in to your account manually to verify any suspicious claims in the strange email. 🚫
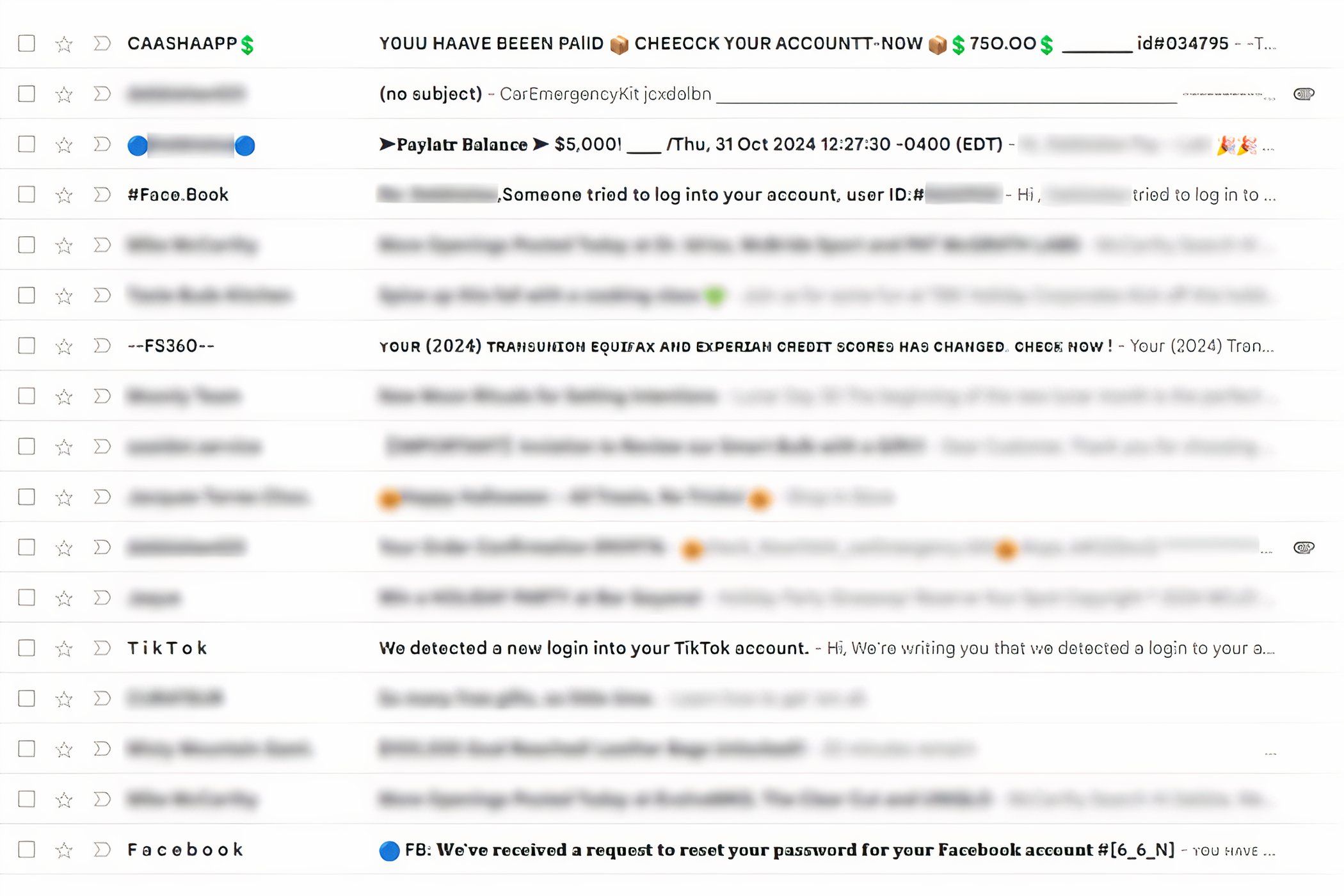
A more obvious red flag to look out for is when the email subject or sender has some kind of strange font, unnecessary emojis, or odd spacing around the company or sender name (like PAYPAL instead of just PayPal). This tactic is so obvious that I'm surprised hackers still bother to do this. spam filters automatically prevent these types of emails from entering my inbox, but if you see them in yours, definitely avoid them! 🛑
Common phishing scams to watch out for
When social engineering is in game, hackers want you to react out of fear. They are trying to manipulate your emotions. One of the most popular ways to get you to react without thinking is by making you believe that someone has accessed your bank accounts. Phishing scams that appear to come from PayPal or your internet service provider are very common. services banking are extremely common. 💰
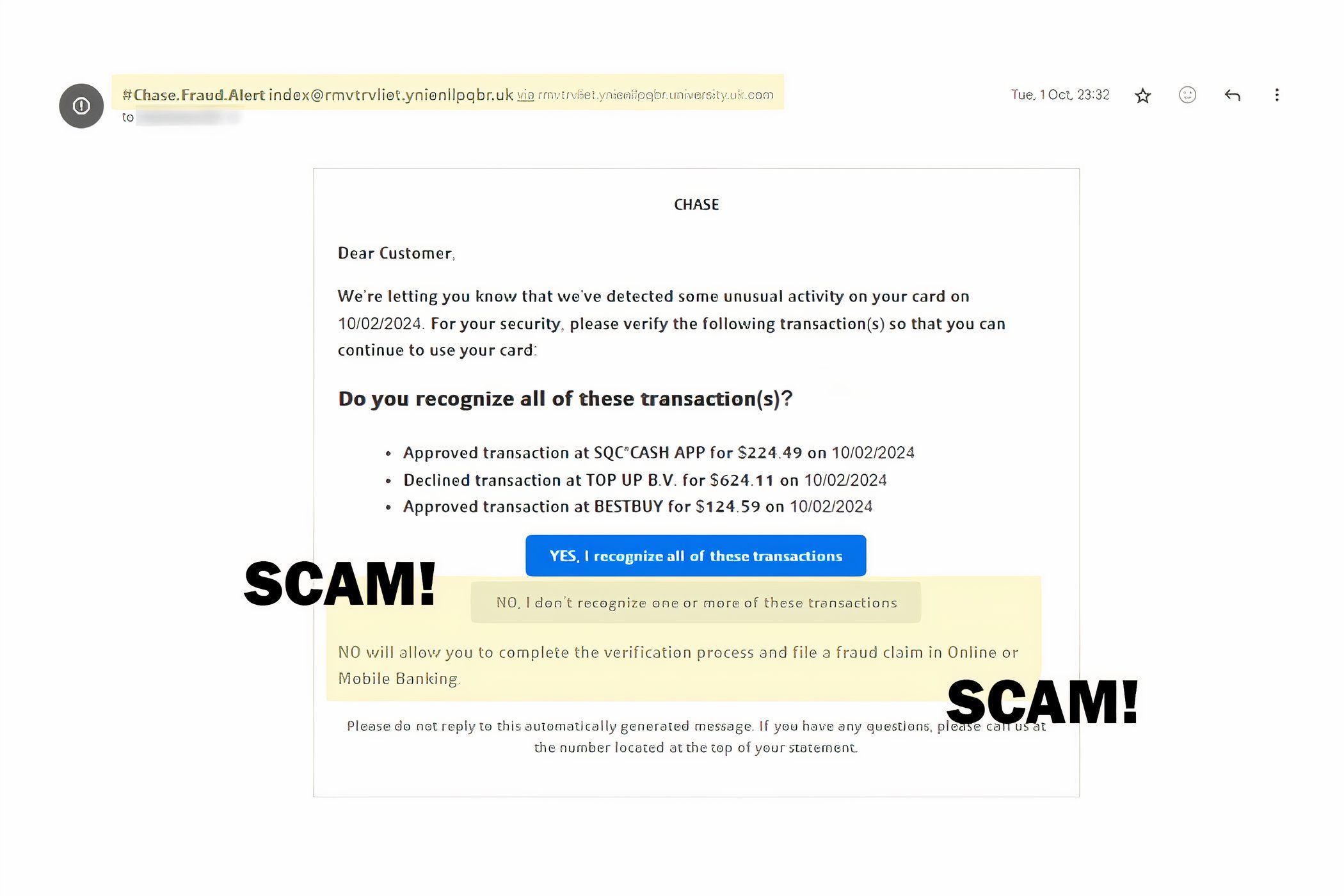
If you receive something like this, do not click on the link! Check the status of your account by manually accessing it through a trusted method, or call your bank's customer service number directly. 📞
Another method spammers use to make you react impulsively is to make you believe that someone has accessed your social media accounts. 📱
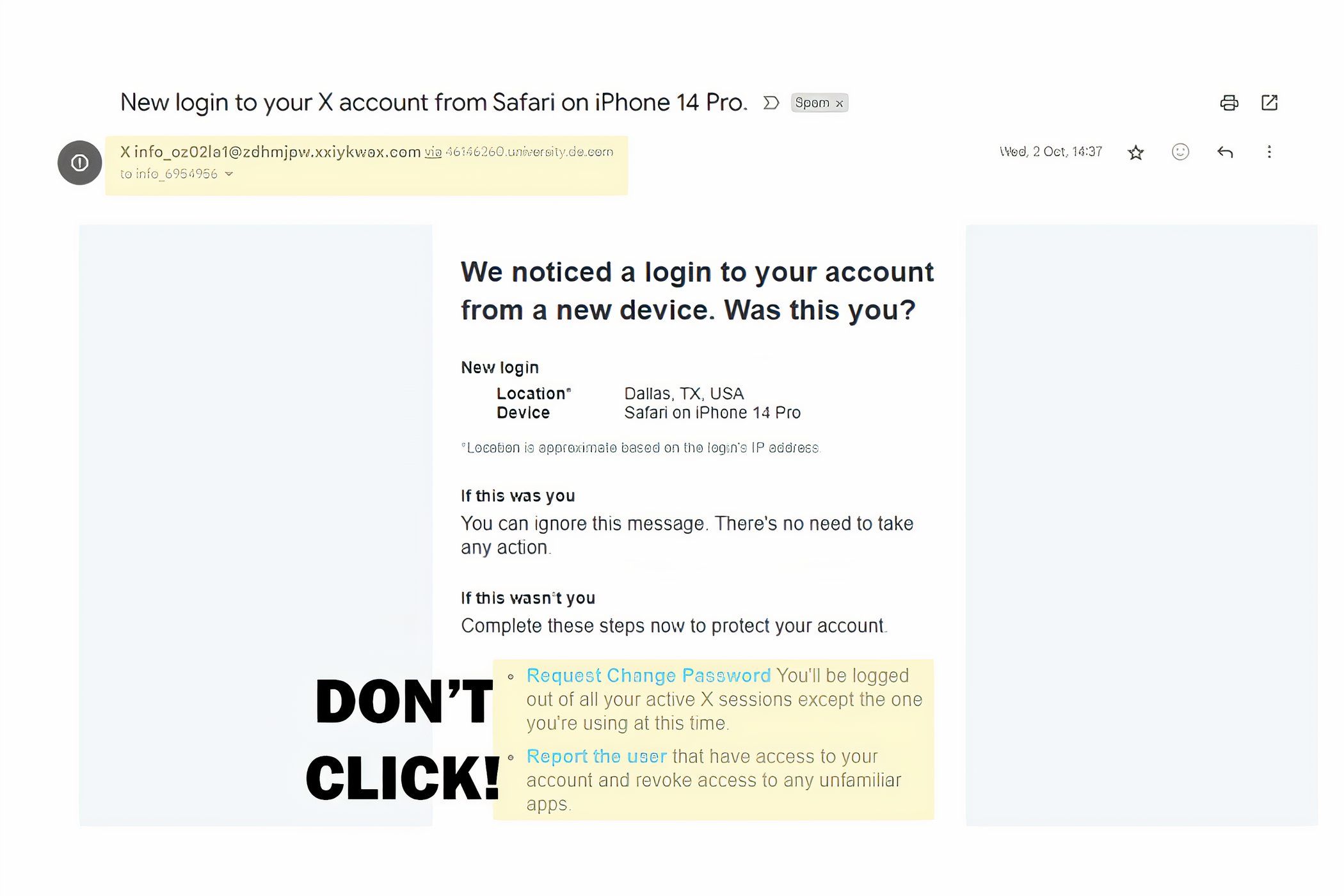
The solution is the same: check the status of your account from another shape. Not through the link in the email. The best way to keep up to date sure is to assume the worst. Never click or download anything from an email sender that looks suspicious or unexpected. ⚡
The unfortunate side of social engineering is that the only person who can save you from yourself is you. But that's also empowering! The only person who can really protect you is you, so stay on top of the latest scams. phishing and protect yourself from making a bad decision in the heat of the moment. 🔒